- Details
- Person Name: Scott Davis
HARRISBURG, PA — The Cybersecurity Association of Pennsylvania is warning residents about a dangerous phishing scam targeting Pennsylvanians via text message. The fraudulent message claims to be a final notice from the “Commonwealth of Pennsylvania Motor Vehicles (DMV),” threatening penalties for an alleged unpaid traffic ticket. However, the details of the message reveal it to be a scam designed to steal personal and financial information.
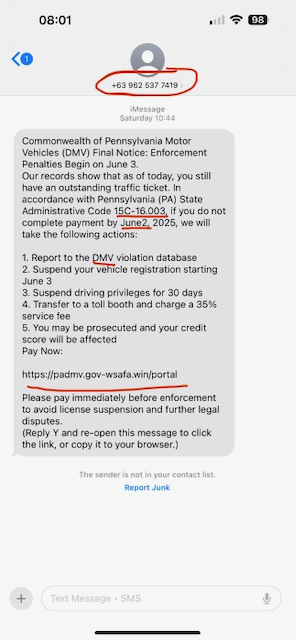
The text message, which appears to originate from the international phone number +63 962 537 7419 (a Philippines-based number), urges recipients to pay immediately via a suspicious link: https://padmv.gov-wsafa.win/portal. This domain is not affiliated with any official government agency and uses a “.win” extension, rather than the legitimate “.pa.gov” or “.gov” domain used by real government sites.
The message references a statute — “15c-16.003” — which does not exist in Pennsylvania’s administrative code, further confirming its fraudulent nature. It also uses improper formatting, such as “June2, 2025” without appropriate spacing, and inaccurately refers to the state agency as the “DMV.” In Pennsylvania, the Department of Motor Vehicles is known as PennDOT (Pennsylvania Department of Transportation), and does not issue traffic violation notifications or collect payments through unsolicited text messages.
The message claims that failure to comply will result in severe penalties, including suspension of vehicle registration, loss of driving privileges, prosecution, and even damage to the recipient’s credit score — all tactics designed to instill fear and coerce payment.
“This scam is a textbook example of SMiShing — phishing via SMS,” said a spokesperson from the Cybersecurity Association of Pennsylvania. “It combines urgency, fear, and official-sounding language to deceive people into clicking fraudulent links and submitting personal information. PennDOT does not communicate or request payments this way.”
If you receive a similar message, do not click the link or respond. Instead, report the message as junk or phishing directly from your device. If you have already clicked the link or submitted payment, contact your financial institution immediately, file a report with your local law enforcement agency, and notify the Pennsylvania Office of Attorney General.
Residents are encouraged to stay vigilant and remember: government agencies will never request payment or personal information via unsolicited text messages. Always verify the source before responding to any digital communication involving sensitive data.
For more information and ongoing scam alerts, visit the Cybersecurity Association of Pennsylvania online.
- Details
- Person Name: Scott Davis
The FBI has issued a public cybersecurity bulletin warning that a sophisticated cybercrime group known as the Silent Ransom Group (SRG)—also referred to as Luna Moth, Chatty Spider, and UNC3753—is actively targeting law firms across the United States. This threat actor, operating since at least 2022, has expanded its focus in recent months to specifically victimize legal organizations due to the sensitive nature of the data they manage.
SRG’s method of attack diverges from traditional ransomware models. Instead of encrypting files, the group uses social engineering tactics to gain remote access to systems and exfiltrate data, which it then uses as leverage in extortion campaigns. The FBI notes that the group has become known for its use of phishing emails disguised as subscription service notifications. These emails typically claim that a small subscription charge is pending and instruct the recipient to call a phone number to cancel. During that call, the victim is directed to install legitimate remote access tools—such as Zoho Assist, AnyDesk, or Splashtop—which unknowingly provide attackers with access to their device.
In a concerning shift in tactics observed as of March 2025, SRG has begun impersonating internal IT staff via unsolicited phone calls. The attackers tell employees that IT work needs to be done and direct them to grant remote access to their devices. Once inside, SRG quickly moves to exfiltrate data using tools like WinSCP or Rclone—often without escalating privileges, allowing the attack to proceed unnoticed by antivirus or endpoint detection systems. After extracting sensitive files, SRG contacts the victim organization with ransom demands, threatening to leak or sell the data unless payment is made.
While law firms are currently the primary target, the FBI reports that organizations in the healthcare and insurance sectors have also been affected. Despite claiming to have a public site for posting stolen data, SRG has been inconsistent in actually following through, possibly as a pressure tactic during negotiations.
The FBI emphasizes that SRG’s attacks often leave minimal traces, making them difficult to detect using traditional security tools. Network defenders are advised to monitor for signs such as unauthorized downloads of remote access tools, unexpected outbound data transfers using WinSCP or Rclone, and any suspicious IT-related communications with employees.
To mitigate the risk, the FBI recommends a series of basic but critical steps: implement robust phishing awareness training, enforce multifactor authentication across all systems, maintain clear internal protocols for IT support communications, and ensure regular, secure data backups. Organizations are also encouraged to share any legally permissible information about incidents involving SRG with their local FBI Cyber Squad, including ransom notes, phishing emails, attacker phone numbers, and cryptocurrency wallet details.
This alert serves as a critical reminder for Pennsylvania’s legal and business communities to remain vigilant. The Cybersecurity Association of Pennsylvania continues to monitor developments and urges all members to ensure their systems and staff are prepared to respond to evolving threats like SRG. More information, along with FBI field office contacts, can be found at www.fbi.gov/contact-us/field-offices.
- Details
- Person Name: Scott Davis
As Super Bowl 59 approaches, the excitement is palpable—especially for Philadelphia Eagles fans hoping for another championship run. Whether you're a die-hard Eagles supporter, a Kansas City Chiefs fan, or simply in it for the spectacle (and Taylor Swift’s potential appearance), cybercriminals are leveraging the hype to launch sophisticated scams. From phishing attempts to fake ticket sales, these scams exploit fans’ emotions and urgency, making it crucial to stay vigilant.
- Details
- Person Name: Scott Davis
Today is Groundhog Day, since 1887, it is the one day a year where we rely on a Groundhog named Punxsutawney Phil, to forecast the next six weeks of our lives. In today’s case the forecast calls for 6-more weeks of Winter.
In 1993, the movie Groundhog Day was released where Bill Murray gets trapped in a time loop reliving this Pennsylvania Dutch superstition that a groundhog’s shadow on February 2nd predicts how long winter will last.
- Details
- Person Name: Scott Davis
As we kick off Data Privacy Week, the Cybersecurity Association of Pennsylvania wants to bring attention to a critical and growing issue: AI Data Security. In today’s world, artificial intelligence has become an integral part of everyday life, both for consumers and businesses. From Apple Intelligence on your iPhone to Google’s Gemini, Meta AI, ChatGPT, and emerging platforms like DeepSeek, AI is shaping the way we interact with technology.
While AI offers unparalleled speed and accuracy in answering questions and solving problems, it also introduces risks, particularly in how it processes, learns from, and uses data.
- Details
- Person Name: Scott Davis
TikTok Ban in the U.S.: Access Blocked and Cybersecurity Risks Intensify
The TikTok ban in the United States has officially gone into effect, and TikTok engineers appear to have implemented robust measures to block access to the app for users within the country. This unexpected level of restriction has caught many by surprise, as it extends even to those attempting to bypass the ban using Virtual Private Networks (VPNs).
- Details
- Person Name: Scott Davis
The Supreme Court has upheld the federal Protecting Americans from Foreign Adversary Controlled Applications Act, effectively banning the Chinese-owned social media platform TikTok in the United States. The decision, delivered just days before the law takes effect, emphasizes the growing concerns over cybersecurity and data privacy, sparking a critical conversation about the handling of user data and national security risks.
- Details
- Person Name: Scott Davis
As TikTok faces potential bans in various regions, many users are turning to RedNote, a Chinese social media platform gaining rapid popularity. While the app promises a vibrant and engaging space for creative content, it’s essential to be aware of the potential risks involved. Below, we explore critical security concerns, data privacy issues, and the emerging threat of deepfake technology associated with the app.
- Details
- Person Name: Scott Davis
In the face of natural disasters, small businesses often find themselves at a crossroads, grappling with the challenges of maintaining operations amidst chaos. Winter weather, hurricanes, and even wildfires present unique threats that can disrupt business continuity and jeopardize the very existence of a small enterprise. However, with strategic planning and a deep understanding of critical concepts such as Recovery Time Objective (RTO), these businesses can navigate through adversity and emerge resilient.

